Using a remote keystore provider
DataStax Enterprise (DSE) database uses the Java Cryptography API (JCA) to implement SSL providers.
The JCA is a pluggable architecture that abstracts the actual cryptography implementation from the algorithm requested.
To support swapping out different implementations, DSE database uses Cipher.getInstance("AES").
The JCA architecture Provider class allows multiple implementations to register using a different service provider interface (SPI).
Java comes with multiple providers and supports installation of additional providers, such as PKCS12.
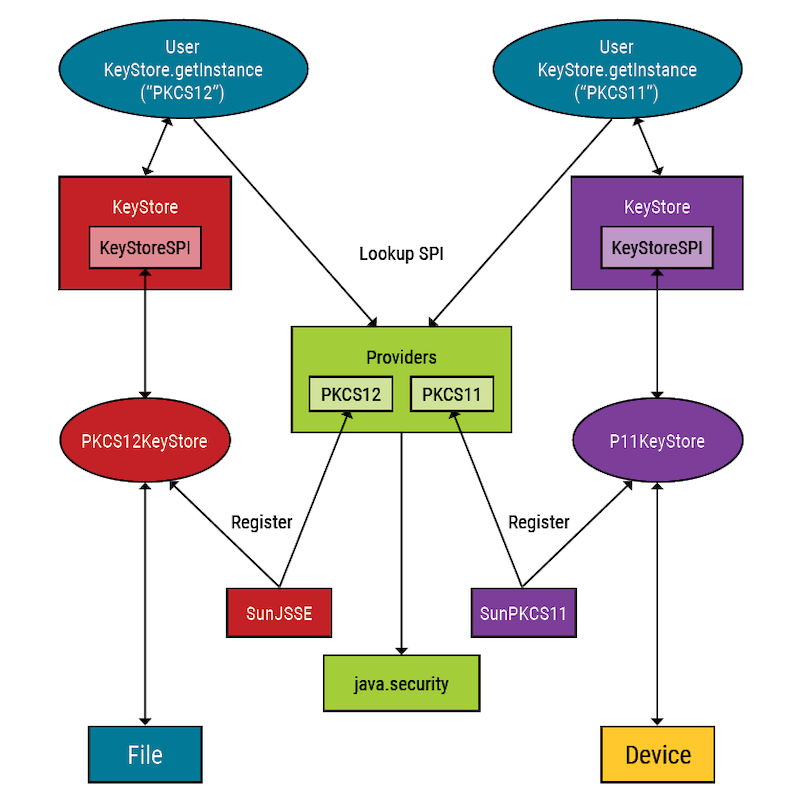
Considerations for PKCS12 and PKCS11
PKCS11 and PKCS12 are part of the RSA Public Key Cryptography Standards for storing private key and certificate information.
-
PKCS12
-
PKCS11
PKCS12 is typically used to store private key and certificate information on files.
The default keystore type in Java is JKS, though you can specify PKCS12 with the -deststoretype option when creating a keystore with keytool.
For PKCS12 in DSE, set the desired SPI in the truststore_type property in cassandra.yaml.
The valid truststore types are JKS (default), JCEKS, or PKCS12 (recommended for file-based truststores).
|
Due to an OpenSSL issue, PKCS12 truststores generated with OpenSSL can be incompatible with DSE. For example, a truststore generated with the following command might not work with DSE: However, if you generate a truststore with Java’s
|
PKCS11 provides an interface to connect with hardware keystore devices.
This type of keystore can store private keys, secret keys, and certificates like PKCS12, but is designed for Hardware Storage Modules (HSM).
For PKCS11 in DSE, set the keystore_type property in cassandra.yaml.
Valid keystore types are JKS (default), JCEKS, PKCS11, PKCS12 (recommended for file-based keystores).
If you select PKCS11, note the following:
|
DataStax supports To use
|
Install additional providers
Install providers using the java.security configuration that comes with the JRE.
|
For more detailed instructions, see the Oracle documentation on how to implement a provider and the JDK 8 PKCS#11 Reference Guide. |
Add the location to the java.security configuration file, which is located in $<JAVA_HOME>/lib/security/java.security.
The following example assumes an environment where PKCS11 is the keystore type for a Apache Cassandra-only workload:
security.provider.10=sun.security.pkcs11.SunPKCS11 <path-to-pkcs11-provider-config-file>If the PKCS11 configuration file is located at /opt/bar/cfg/pkcs11.cfg, then the complete entry is as follows:
security.provider.10=sun.security.pkcs11.SunPKCS11 /opt/bar/cfg/pkcs11.cfg